Partly in response to the ransomware attack on the NHS, and aimed at bringing the European Union’s Network and Systems Infrastructure directive into UK law by May 2018, the Department of Culture, Media & Sport (DCMS) has stated that the system of fines, which is currently the subject of a consultation to which affected organisation are encouraged to contribute, will remain in place following Brexit and may also cover protection against systems failures such as those which affected British Airways earlier this year, which were blamed on a power outage.
More information on the proposals can be found here and the consultation documents are here.
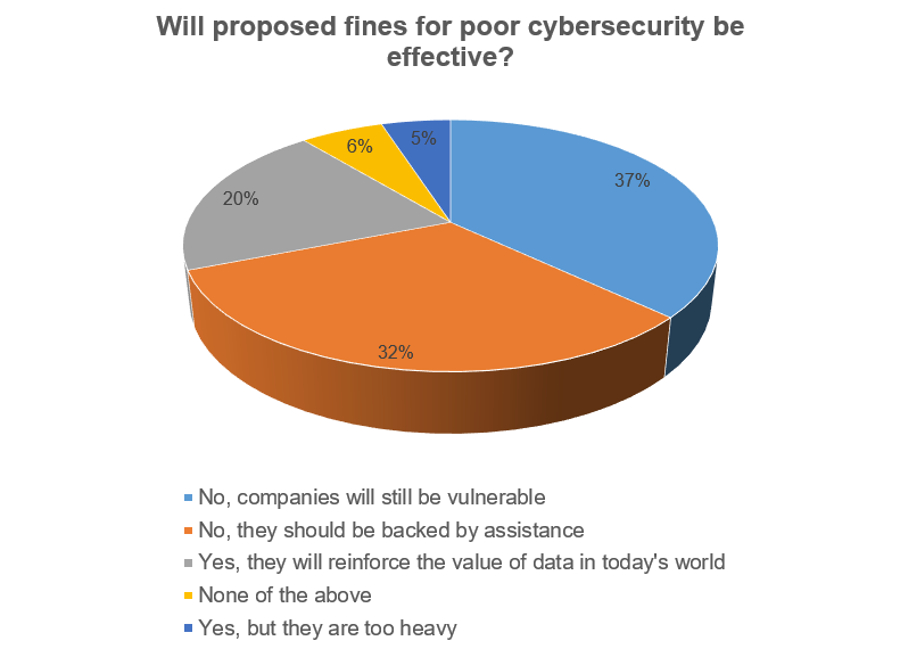
Of the 227 responses, a total of 69 per cent took the view that fines would not be effective and that companies would remain vulnerable (37 per cent), followed by 32 per cent who thought assistance would be more helpful than fines.
A fifth of respondents agreed that the proposed fines would reinforce the value of data, whilst five per cent agreed that fines are a good idea, but that the proposed ceiling of £17m is too heavy. The remaining six per cent failed to find a fit with their opinion, opting for 'none of the above'.
In the debate that followed in Comments, Steve said: "All business nowadays is moving exclusively online, which means we have no choice but to pass over our personal information. Therefore, protection of our data is out of our hands and it’s foolish to think otherwise. No law is going to protect us – it’s just a matter of when we are compromised, rather than if."
"In general security is last on the list for almost every project," added Timothy Murphy. "There is always a pretence and measures are taken for show but it is only the very serious, very big online players who actually design security in properly. This is because every company you can think of is trying to develop a product that’s far too complicated for the amount of people they have working on it."
What do you think? Keep the debate going using Comments below.





Project to investigate hybrid approach to titanium manufacturing
What is this a hybrid of? Superplastic forming tends to be performed slowly as otherwise the behaviour is the hot creep that typifies hot...