NCSC urges vigilance in wake of cyber attack
The National Cyber Security Centre (NCSC) is warning people to remain vigilant in the wake of Friday’s ransomware attack, which affected thousands of computers around the world.

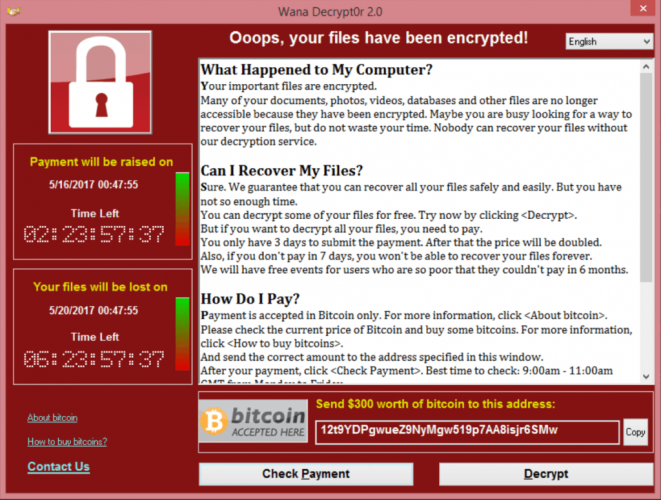
Although there are fears that a new strain of the WannaCry virus could be used to deliver another coordinated attack, the bigger threat is likely to come from machines already infected from Friday’s hack. The NHS was one of several organisations targeted, resulting in patients being turned away from A&E and operations being cancelled.
“Since the global coordinated ransomware attack on thousands of private and public sector organisations across dozens of countries on Friday, there have been no sustained new attacks of that kind,” the NCSC said in a statement.
“But it is important to understand that the way these attacks work means that compromises of machines and networks that have already occurred may not yet have been detected, and that existing infections from the malware can spread within networks. This means that as a new working week begins it is likely, in the UK and elsewhere, that further cases of ransomware may come to light, possibly at a significant scale.”
Register now to continue reading
Thanks for visiting The Engineer. You’ve now reached your monthly limit of news stories. Register for free to unlock unlimited access to all of our news coverage, as well as premium content including opinion, in-depth features and special reports.
Benefits of registering
-
In-depth insights and coverage of key emerging trends
-
Unrestricted access to special reports throughout the year
-
Daily technology news delivered straight to your inbox






Water Sector Talent Exodus Could Cripple The Sector
Maybe if things are essential for the running of a country and we want to pay a fair price we should be running these utilities on a not for profit...